FAQs
1. Windows Login
NO. GoTrust ID computer login will function in connection with a specific authentication server, such server will be installed in the enterprise on-premises or cloud environment and managed by enterprise. If your company has Azure AD environment, you can plug-n-play Idem Key for Azure AD managed Windows device without a building authentication server.
GoTrust ID computer login can support Windows and MacOS, not Linux OS.
GoTrust ID supports Windows Azure AD, Active Directory (AD) or Hybrid environments.
Yes, your phone will communicate via BLE automatically if PC is offline. Besides phone, security key – Idem Key is a recommended login method if internet connectivity is limited.
User can login using an Idem Key under various scenarios, or ask for a designated security code from corporate administrators to complete login. Don’t worry, security code from administrator also supports offline login.
Yes, phone and Idem Key can use for both online and offline login. GoTrust ID phone app provides internet or BLE connection, and we manufacture our own USB security key – Idem Key to provide consistent user experiences.
Yes, GoTrust ID supports Windows 10 version 1809 above and Windows 11.
Yes, GoTrust ID supports Windows Server 2016 and 2019. In Windows Server environment, GoTrust ID phone authenticator will not support BLE communication, it must be internet connected.
Microsoft ended support for Windows Vista on April 11, 2017, ended support for Windows XP on April 8, 2014 and ended support for Windows 7, and Windows Server 2008 on January 14, 2020. Upgrading to a supported version of Windows is necessary for security concerns.
GoTrust ID mobile application supports iOS 10 and above, Android 6 and above.
GoTrust ID provides password-free login experiences for local desktop and Windows Remote Desktop Connection.
GoTrust ID restricts one domain user login on each device and does not support the following login types:
- Shift + right-click “Run as administrator”
- Shift + right-click “Run as different user”
- PowerShell cmdlets
Network Level Authentication (NLA) for Remote Desktop Connection is a recommended security feature in Windows. We encourage users to enable NLA when performing RDP for higher security. When NLA is enabled, the RDP client prompts for primary authentication – password, remote PC login screen will appear after primary authentication is verified, user can login to a remote PC by GoTrust ID phone authentication.
More information about NLA and RDP can be found at the Microsoft site.
Yes. GoTrust ID supports Windows Remote Desktop Connection login.
No. Only Idem Key can be used for GoTrust ID Computer Login.
GoTrust ID Computer Login works with Windows credential provider but cannot be used with other third-party credential providers.
For a better user experience, you can open GoTrust ID mobile app before initiating computer login. Keep GoTrust ID mobile app open to build BLE connection automatically between phone and computer if network is temporarily not available. If the network connection is good, user will receive a notification on mobile to request for login authentication without opening the app.
- In-App Security Code: User can find this code on the mobile.
- Security Code generated from AdminPortal: Ask for this Security Code from corporate IT.
- SMS Security Code: User can receive Security Code from SMS once company has launched SMS service and user’s phone number has been registered in AdminPortal.
- Email Security Code: User can receive Security Code from Email once company has launched Email service and user’s email address has been registered in AdminPortal.
For security reason, a maximum of three (3) SMS messages can be sent within 24 hours.
To improve fingerprint recognition on the phone, you can try removing and then reregistering your fingerprint. Also, when biometrics fail during authentication process, app will also request for passcode to proceed the authentication.
Please allow GoTrust ID to use Touch ID/Face ID, Bluetooth, Camera, etc. while installing GoTrust ID mobile app on your phone. Or go to Settings->GoTrust ID to enable the settings.
Yes, you can use the same Idem Key to perform secure login on Windows device or cloud FIDO-enabled services.
We suggest one Idem Key only registered under one account and kept by one person as his or her own private login key. Each Idem Key is protected by the PIN which is set by the key owner. If you keep this PIN confidential, your device is still safe even the key was lost. Please report to corporate admin immediately to delete your Idem Key authenticator from AdminPortal if you lost the key.
You can only use GoTrust ID phone authenticator or GoTrust Idem Key to login Windows after GoTrust ID enrollment. If you want to keep Windows Hello PIN or Windows Hello Biometrics login options, please configure in the AdminPortal. Please note password is not a login option for Windows version 3.1.4 or later.
Yes, update password dialog box will appear on PC when password expires. Please insert new password in the dialog box to update password on the domain controller, old password will be shown automatically which is hidden behind asterisks (******) for security purpose.
Credential provider won’t be triggered if performing Safe Mode login. To limit the effect of physical attack, you can block non administrators from logging in while Windows is running in Safe Mode.
For example, you can set the registry DWORD value HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\SafeModeBlockNonAdmins to 1, to only allow administrator to perform Safe Mode login.
2. Install and Uninstall for Windows
Yes, Group Policy configuration settings can be applied to GoTrust ID desktop application installation. To create and apply the GoTrust ID desktop application Group Policy Object (GPO):
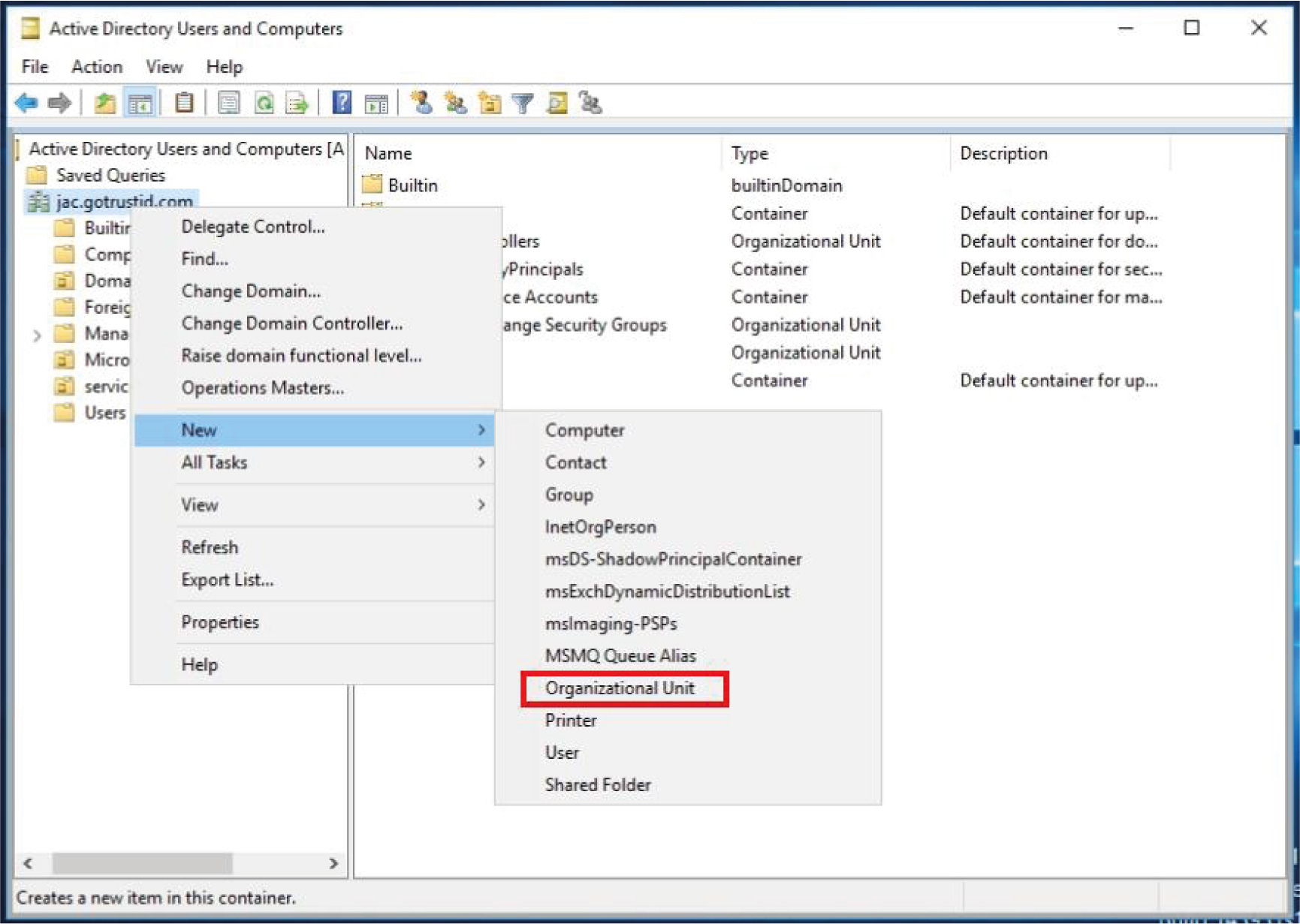
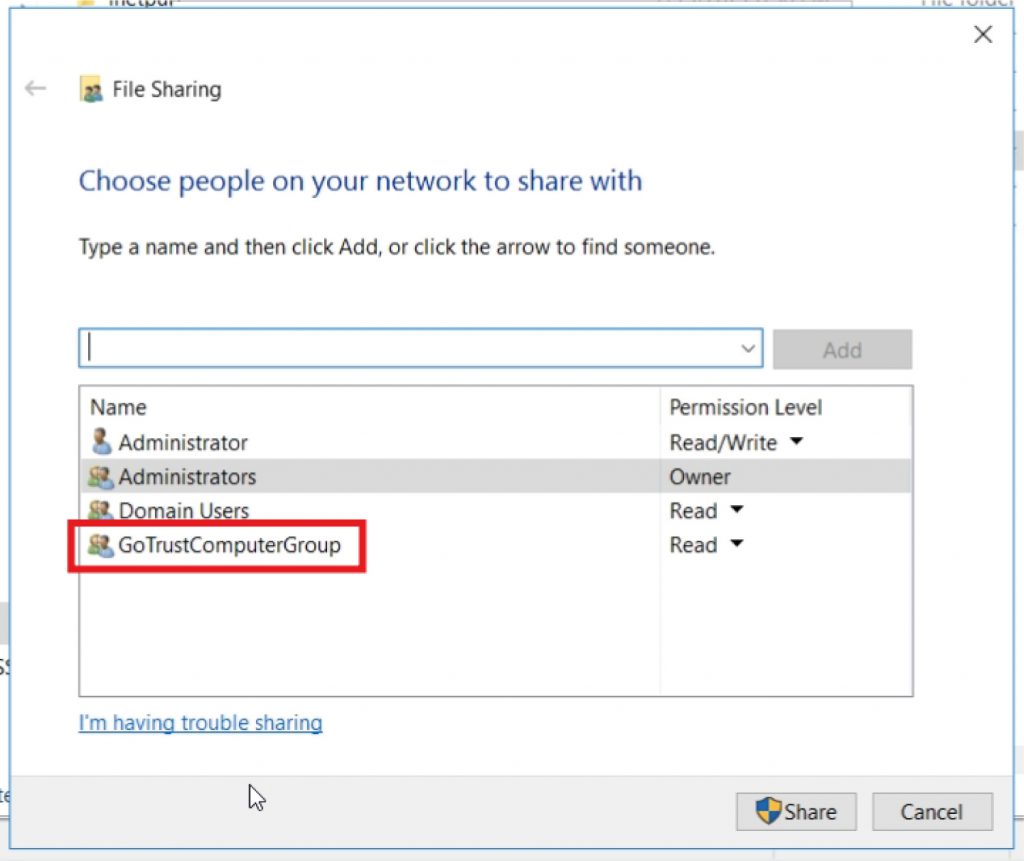
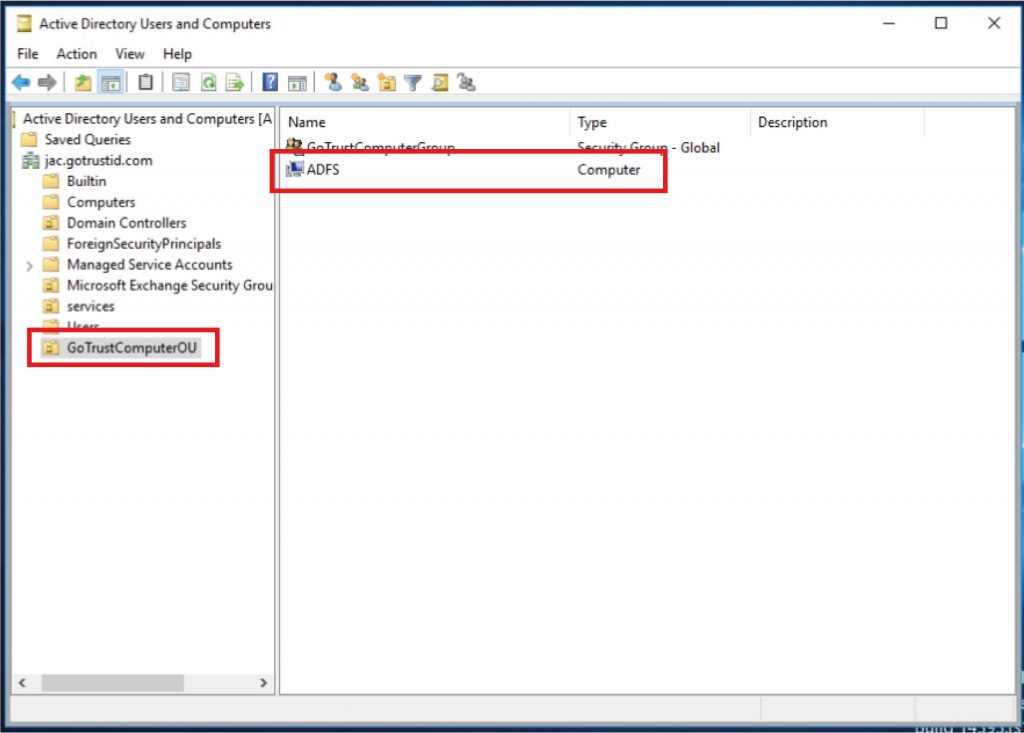
- Go to “Active Directory Users and Computers”, create a new “Organization Unit” under the proper domain.
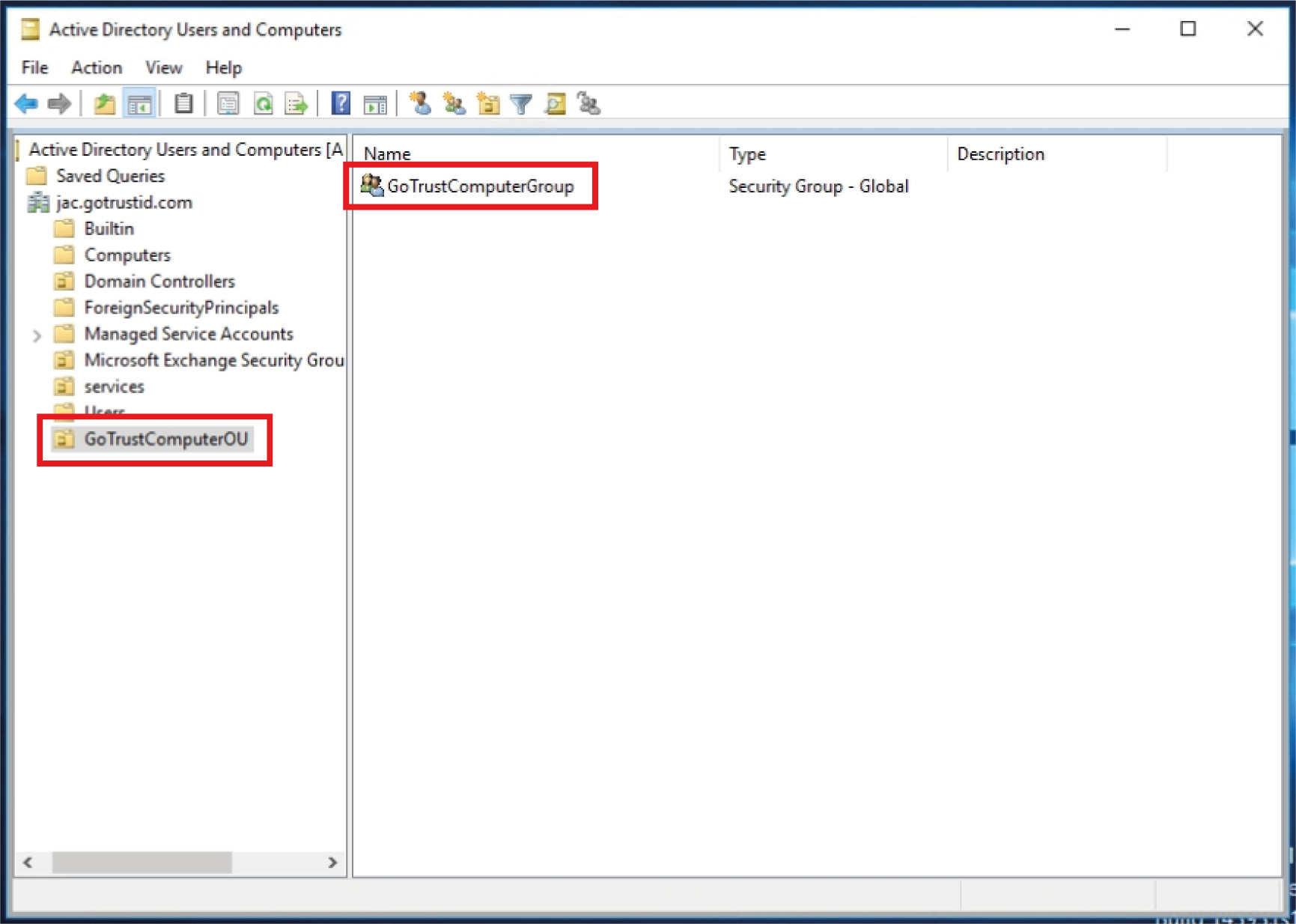
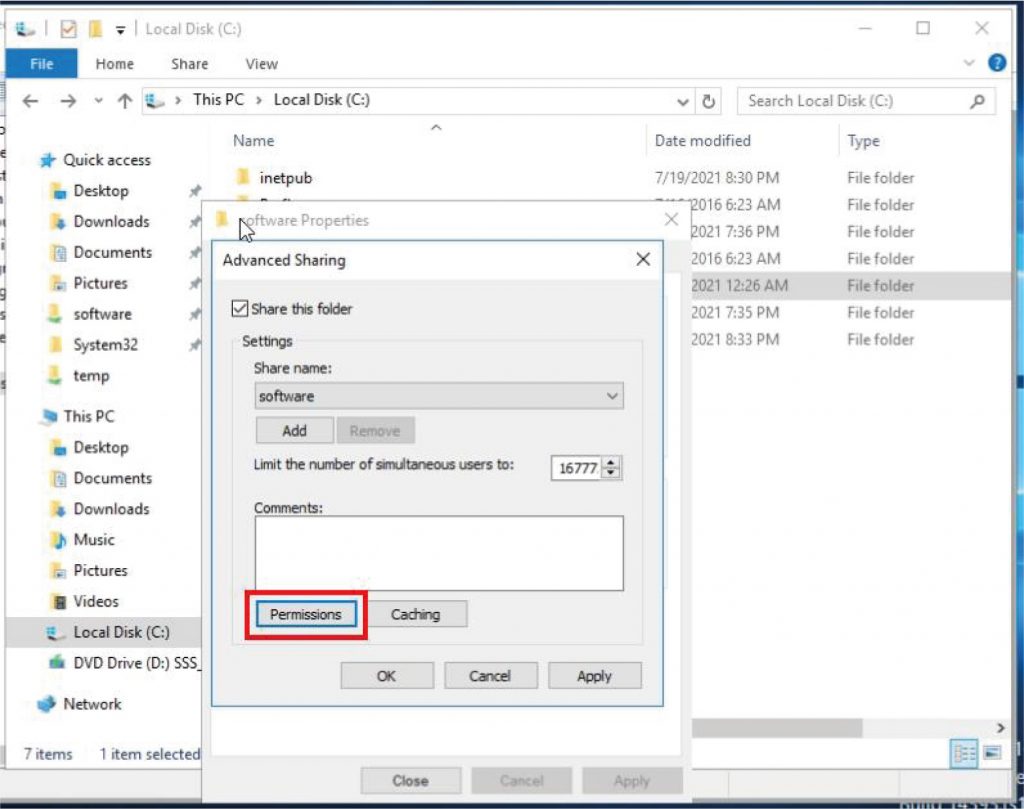
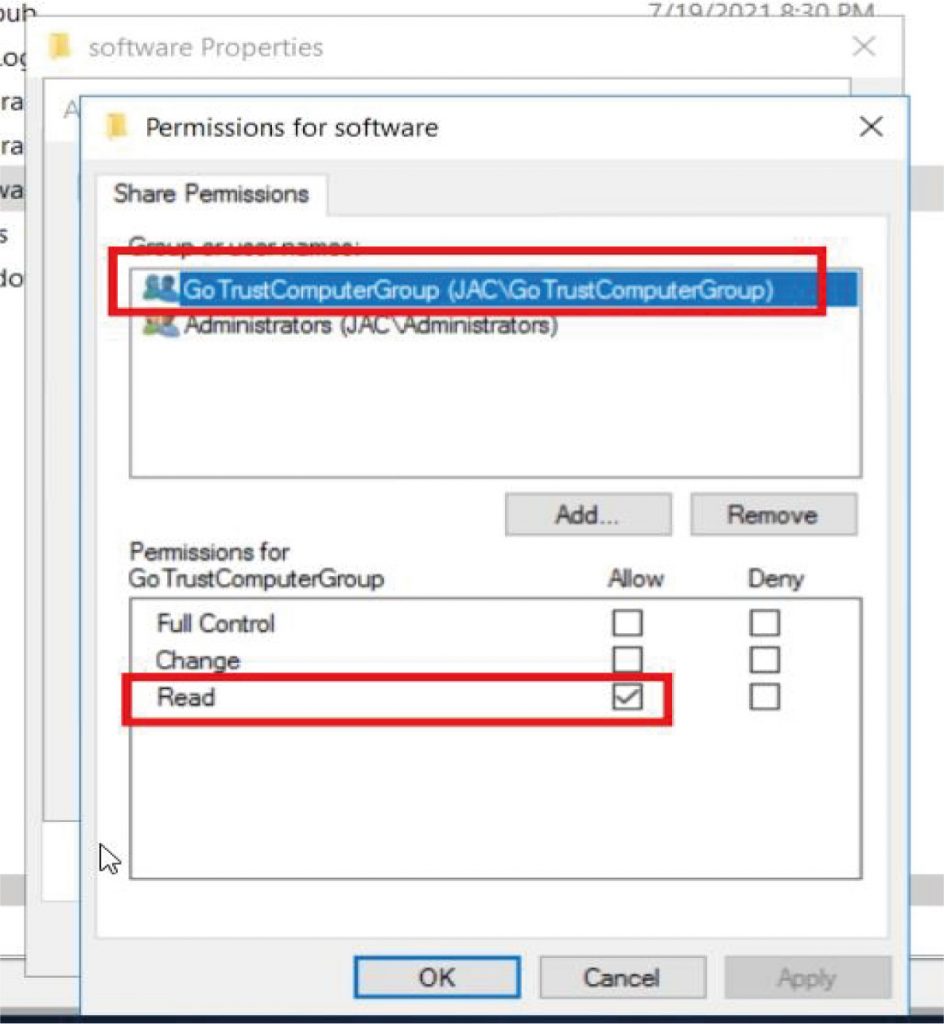
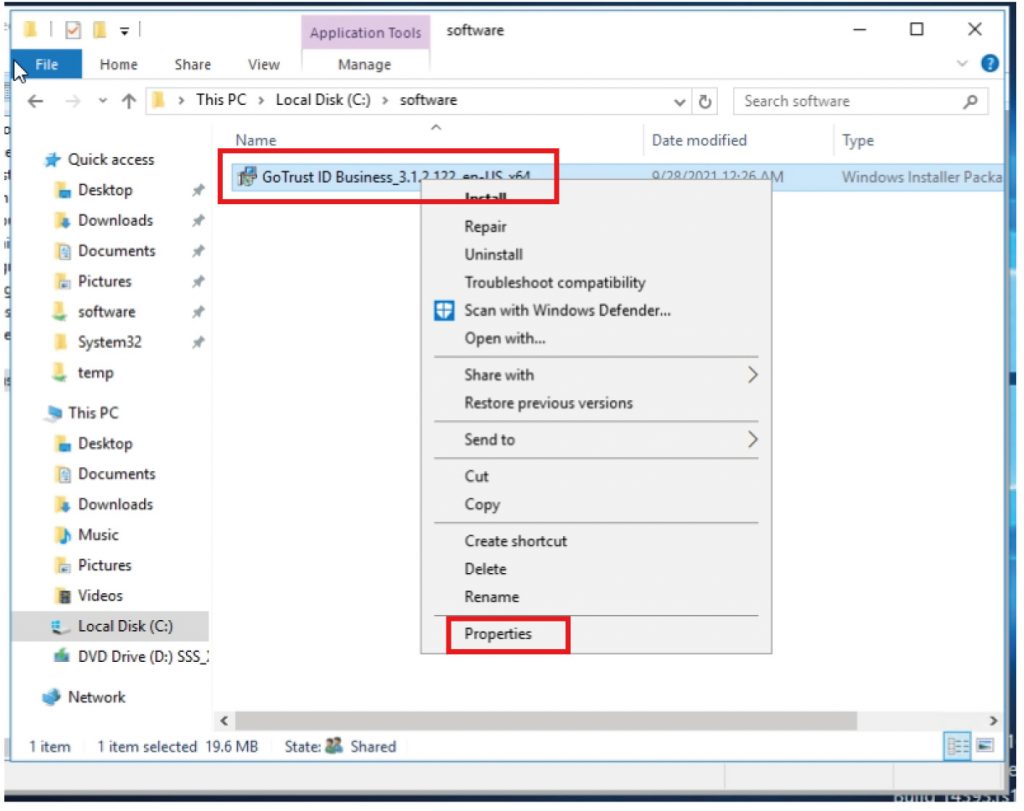
b. b. Right-click the folder where GoTrust ID Business. msi installer is located and click “Properties”, click on the “Sharing” tab to make sure the created Organization Unit has been added. And click “Advanced Sharing” to grant such Organization Unit “Read (& execute)” permission.
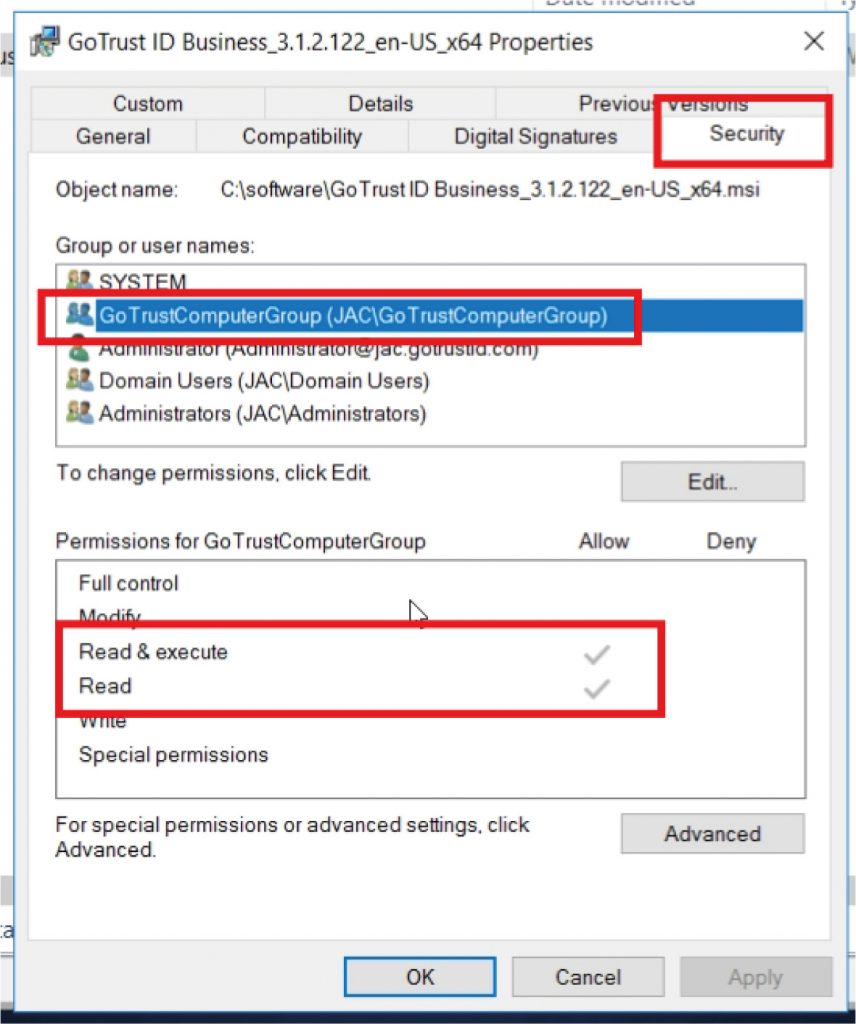
Right-click the GoTrust ID Business. msi installer and click “Properties”, click on the “Security” tab, find the Organization Unit to confirm “Read (& execute)” permission.
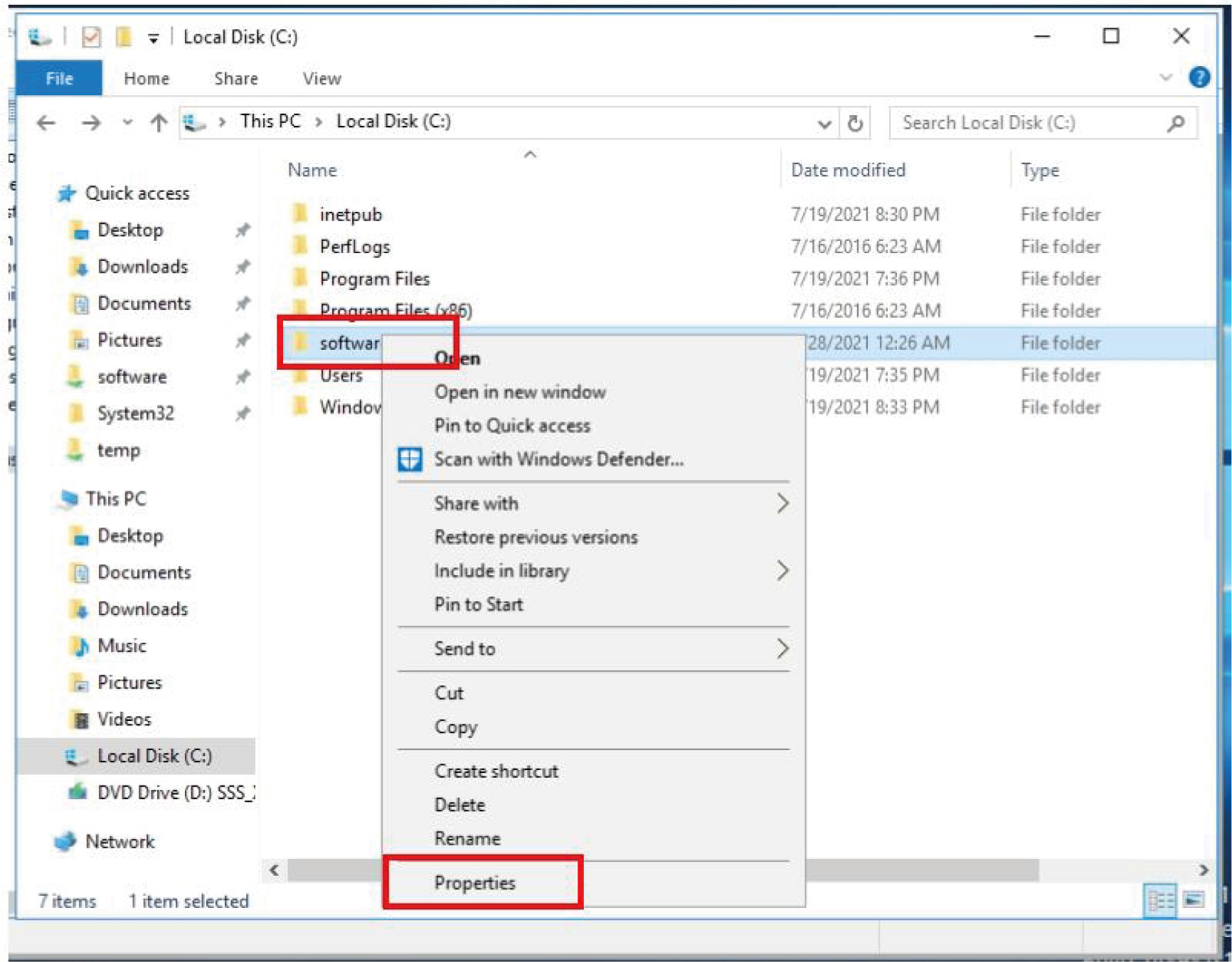
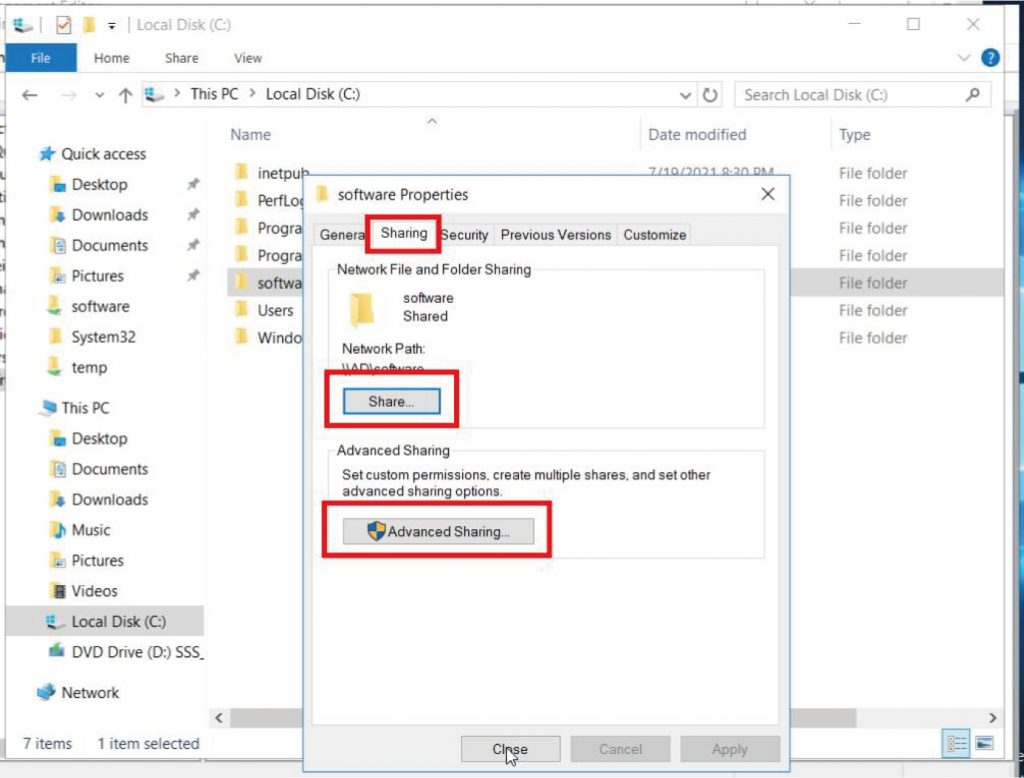
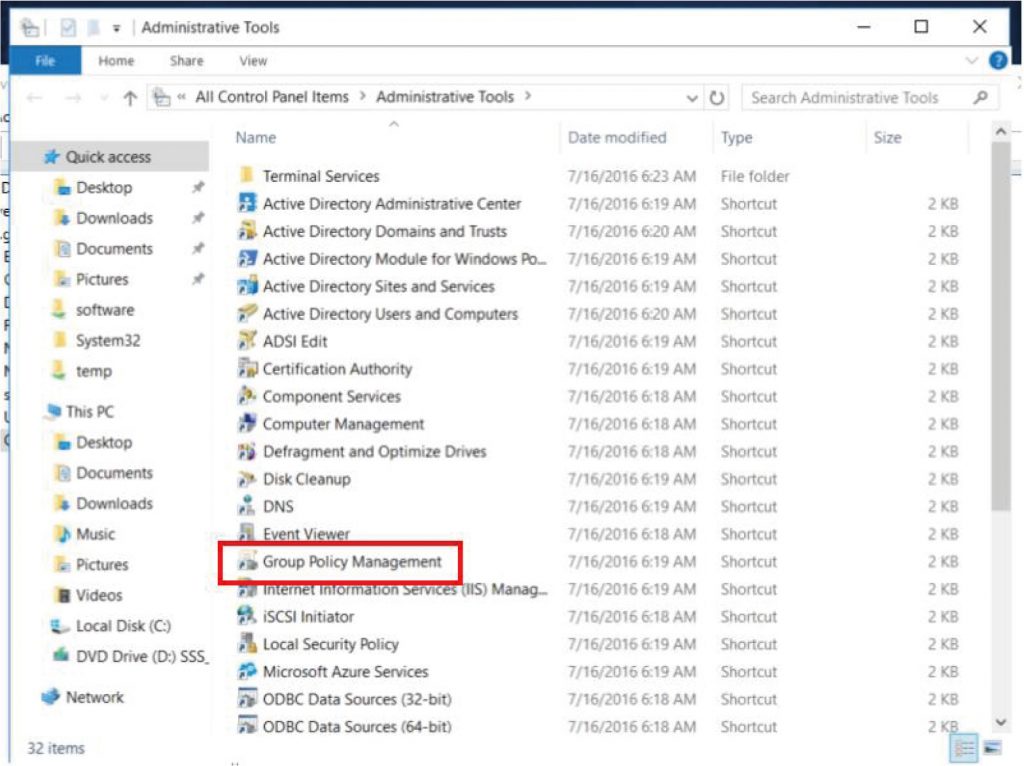
c. Go to “Group Policy Management”, right-click the desired Organization Unit, and click “Create a GPO in this domain, and Link it here”. Right-click the created GPO and click “Edit”.
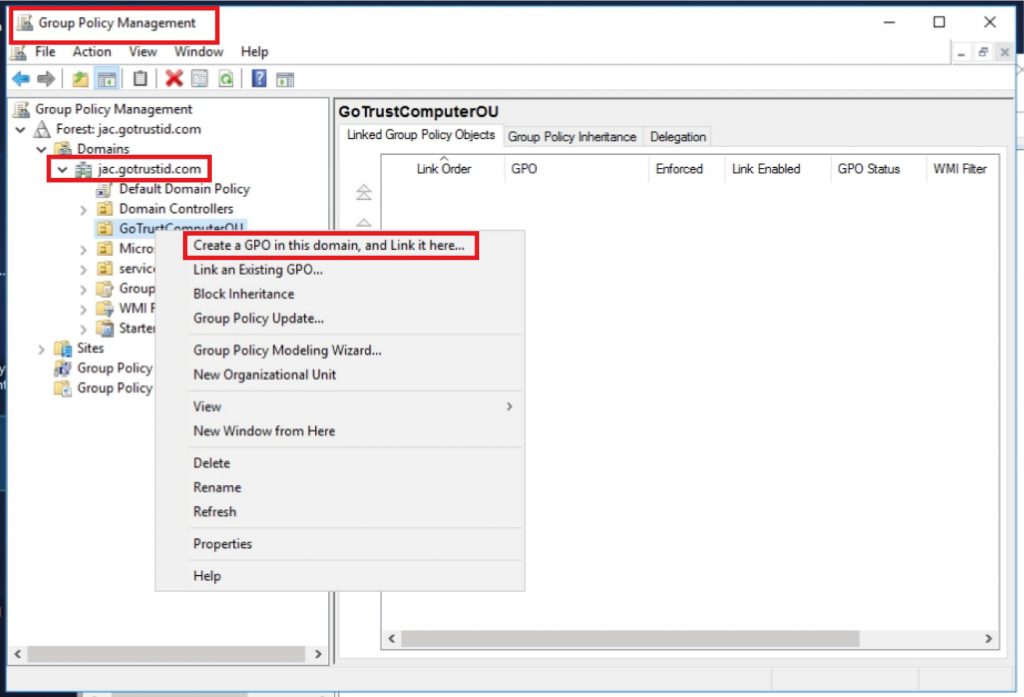
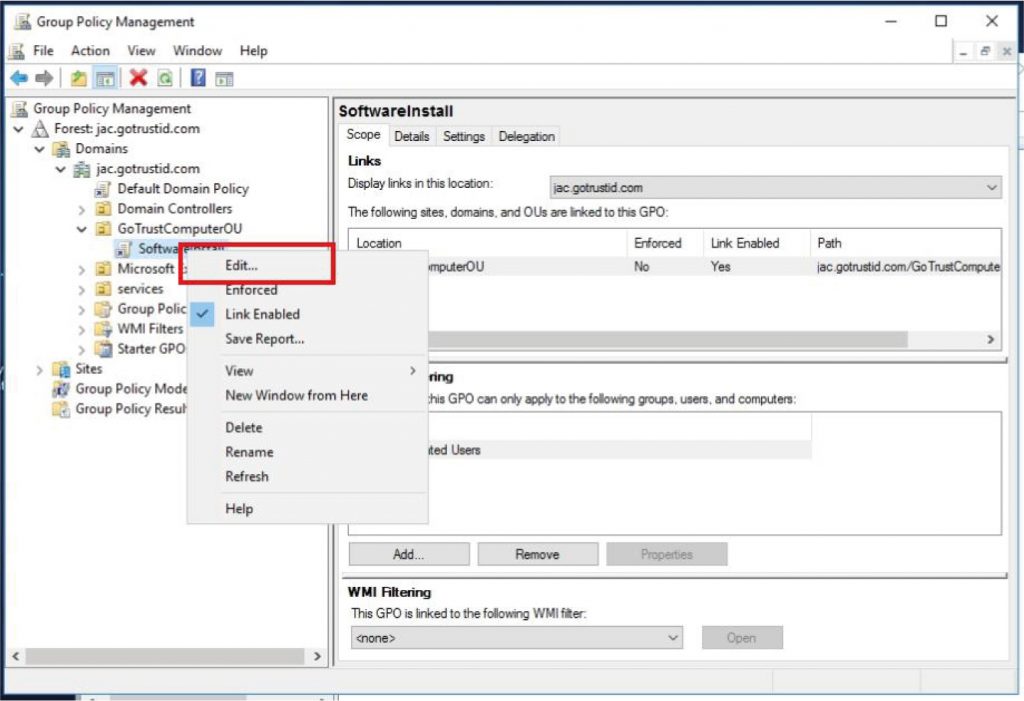
d. Enable following settings and add an environment variable for your authentication server:
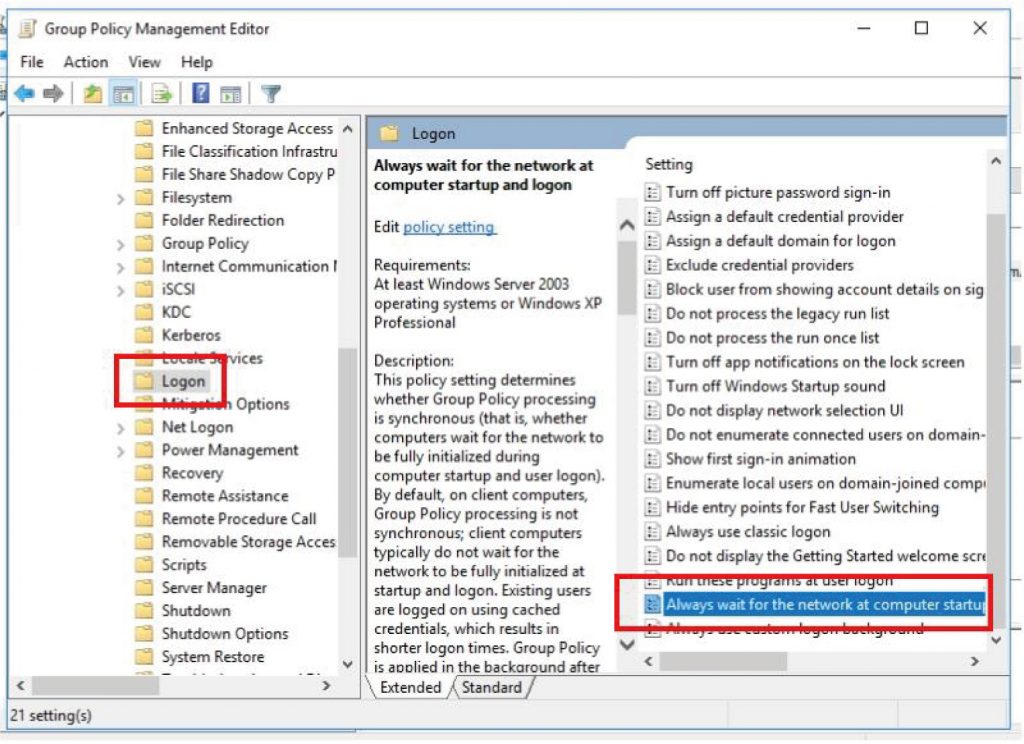
Navigate to “Computer Configurations\Policies\Administrative Templates\System\Logon, enable “Always wait for the network at computer startup”.
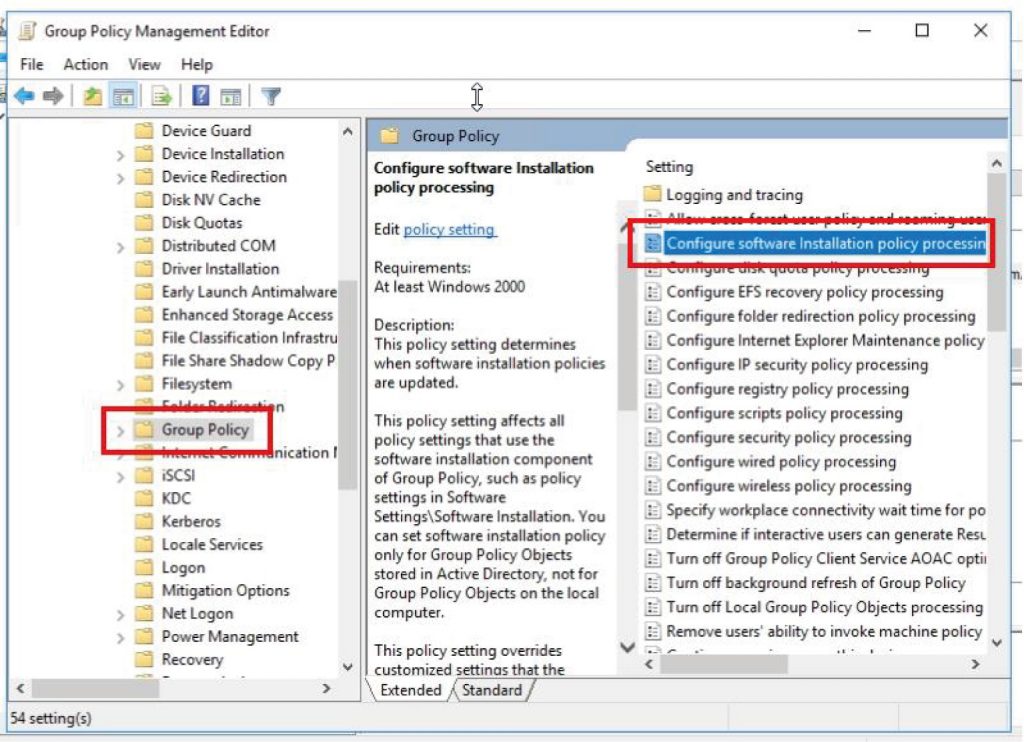
Navigate to “Computer Configurations\Policies\Administrative Templates\System\Group Policy, enable “Configure software installation policy processing”, and ensure the options are all checked.
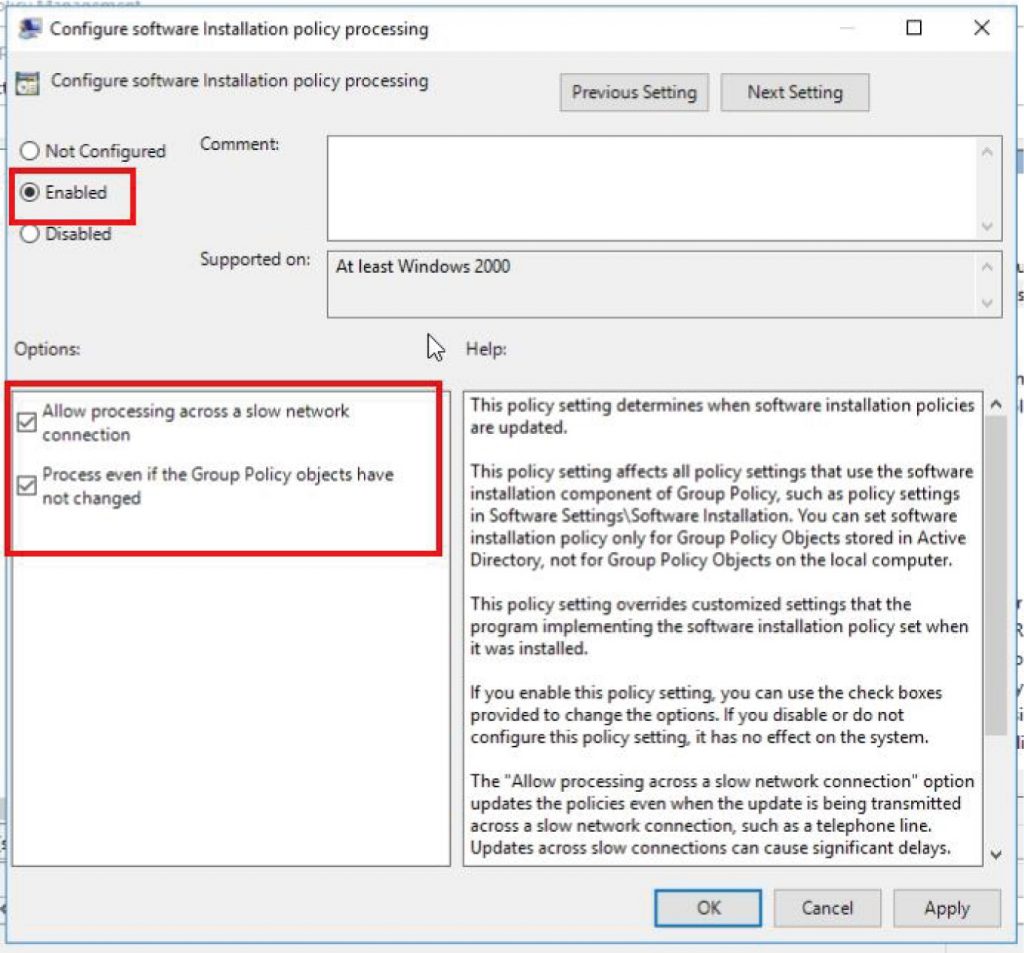
Navigate to “Computer Configurations\Policies\Administrative Templates\Windows Components\Windows Installer, enable “Always install with elevated privileges”.
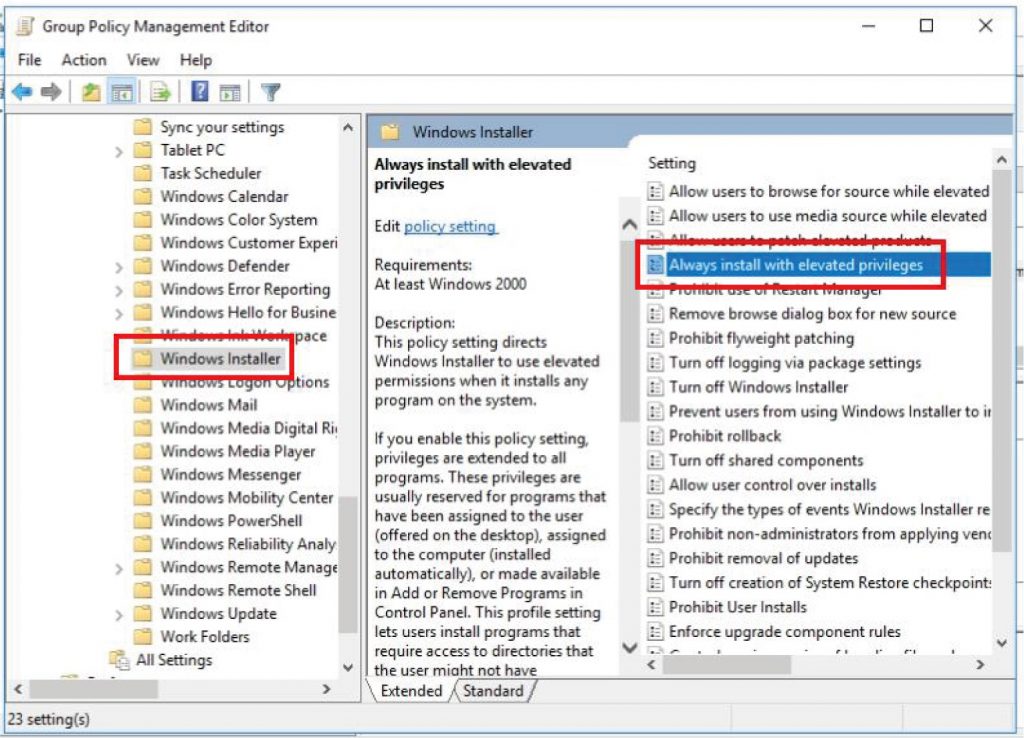
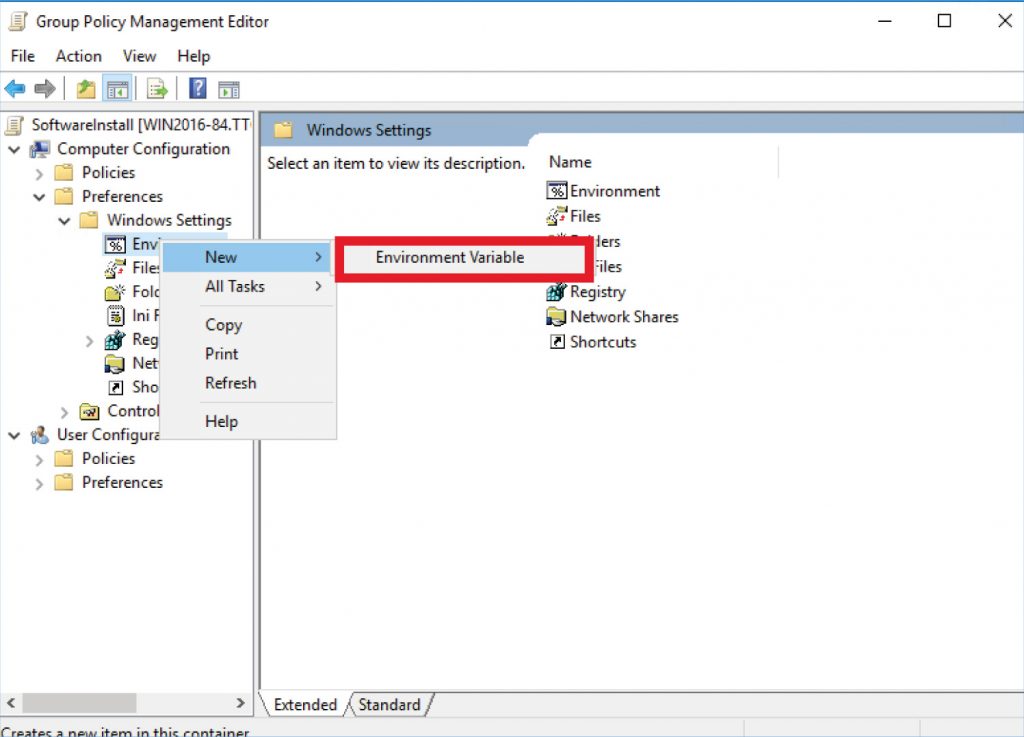
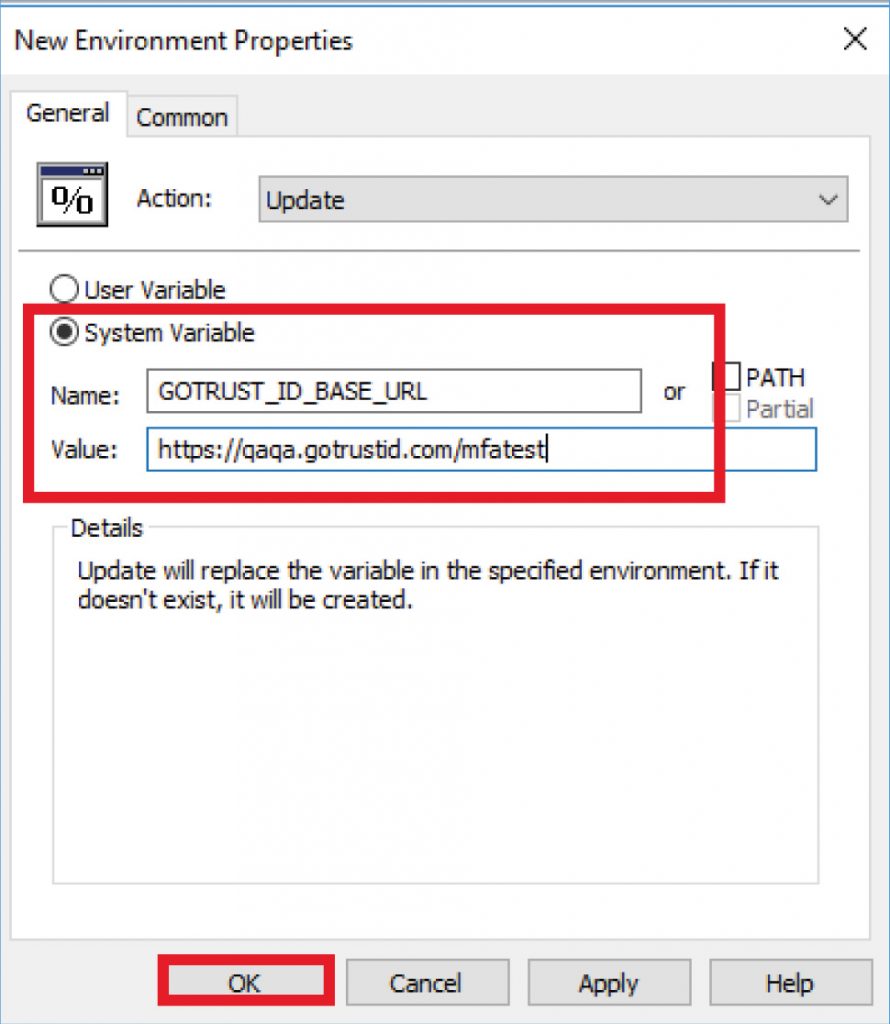
Navigate to “Computer Configurations\Preferences\Windows Settings\Environment”, and right-click “New – Environment Variable” to create a base server URL system variable.
e. Navigate to “Computer Configurations\Policies\Software Settings, right-click “Software installation, click “Package” under “New”.
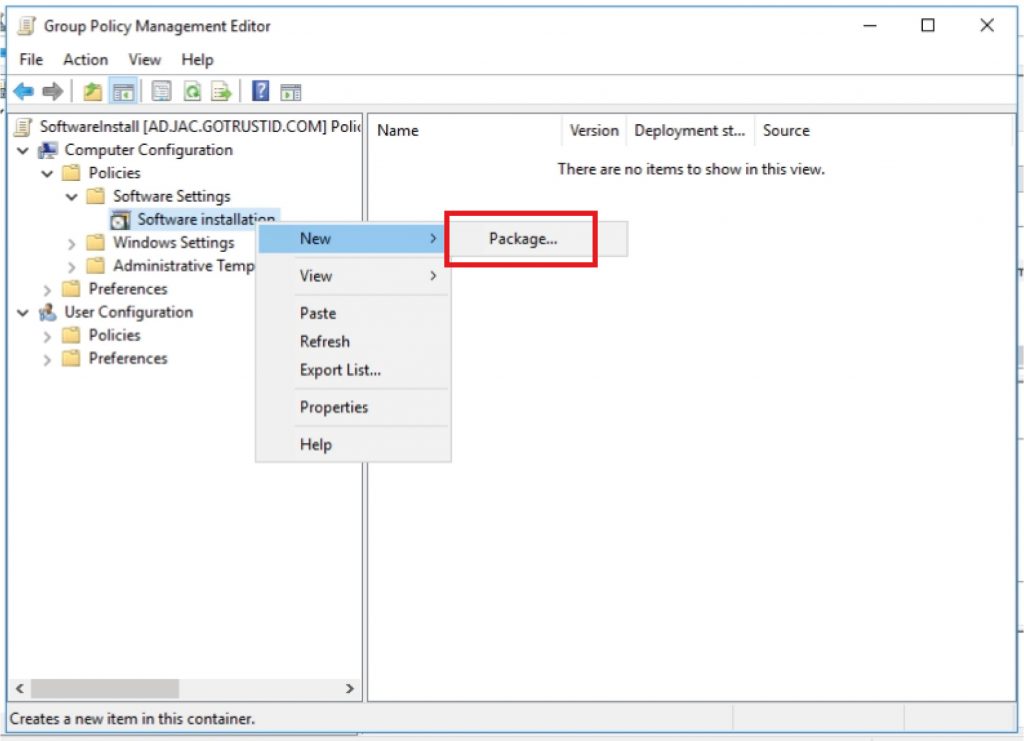
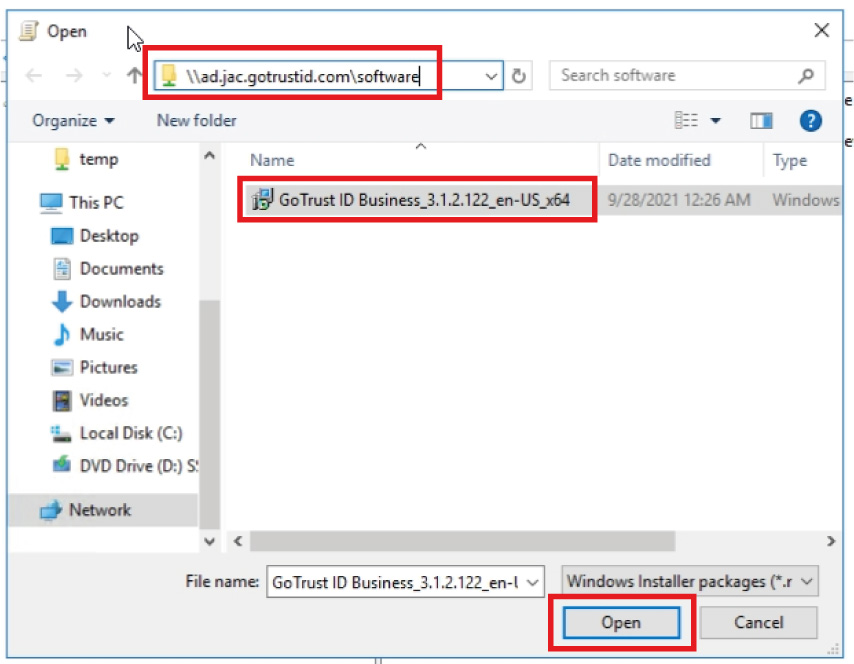
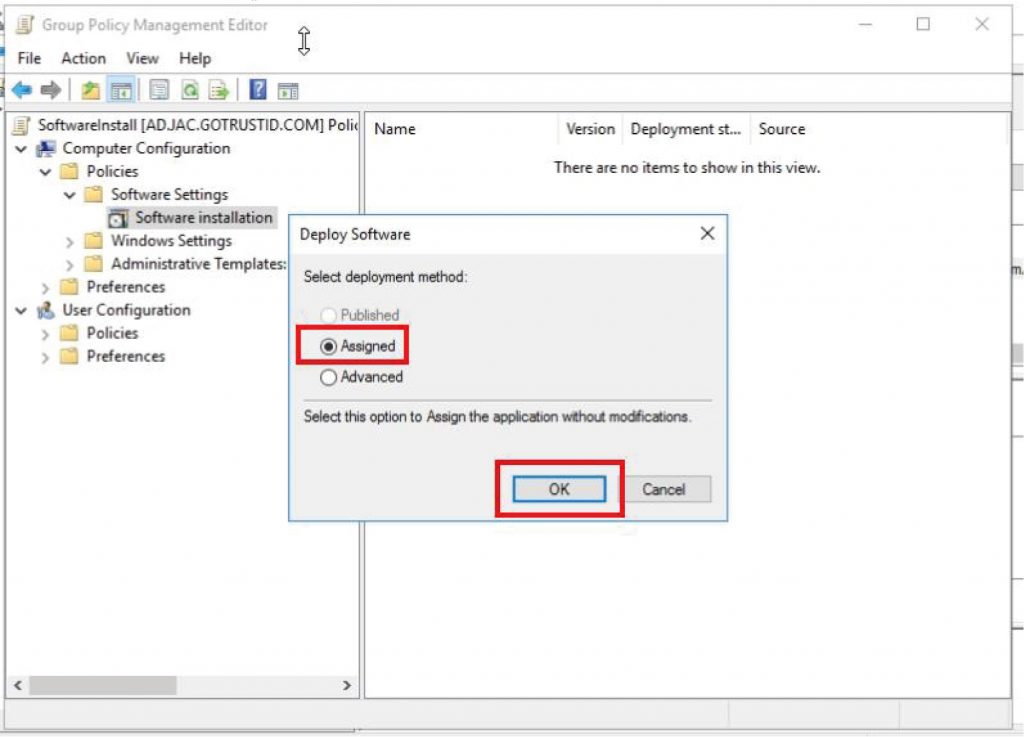
f. Find the GoTrust ID Business. msi installer by the UNC path, e.g. \\server-name\software\GoTrustIDBusiness.msi, and click “Open”, select deployment method “Assigned” and click “OK”.
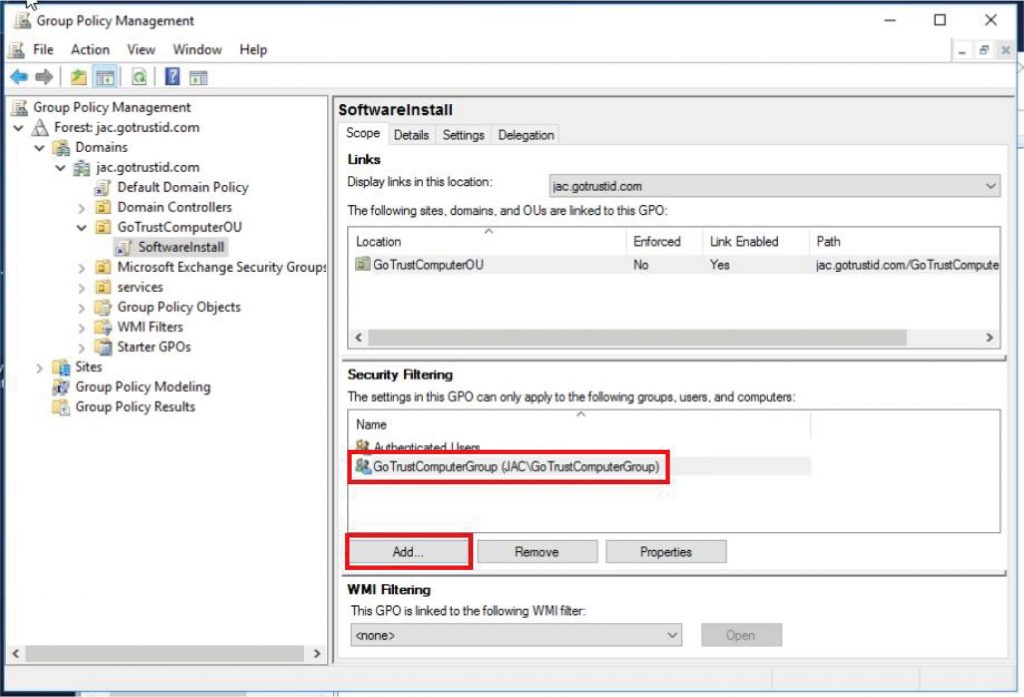
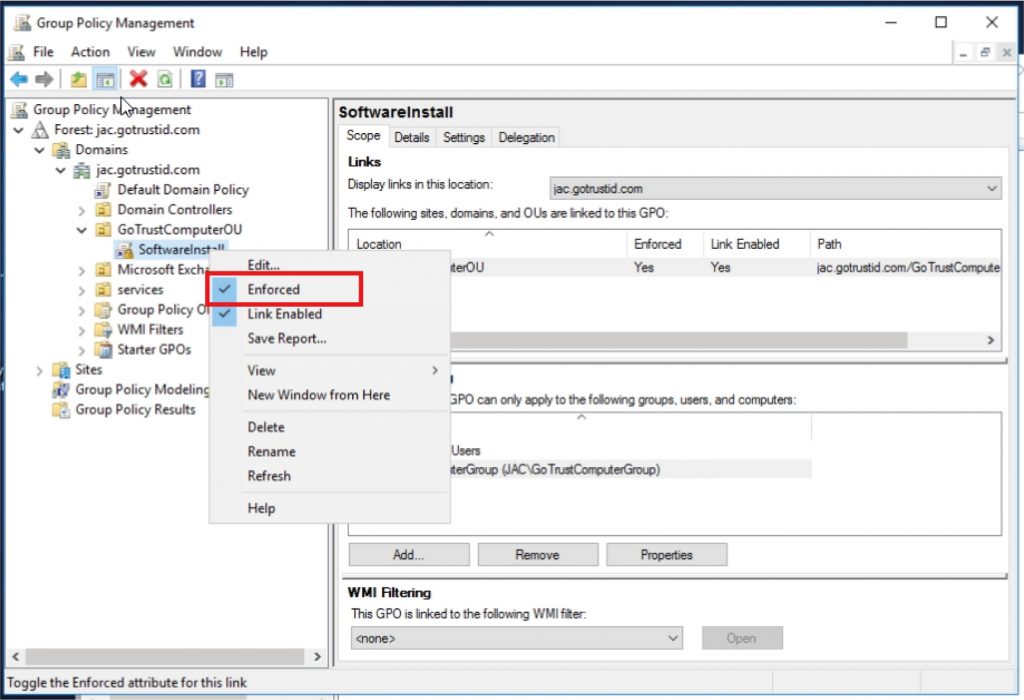
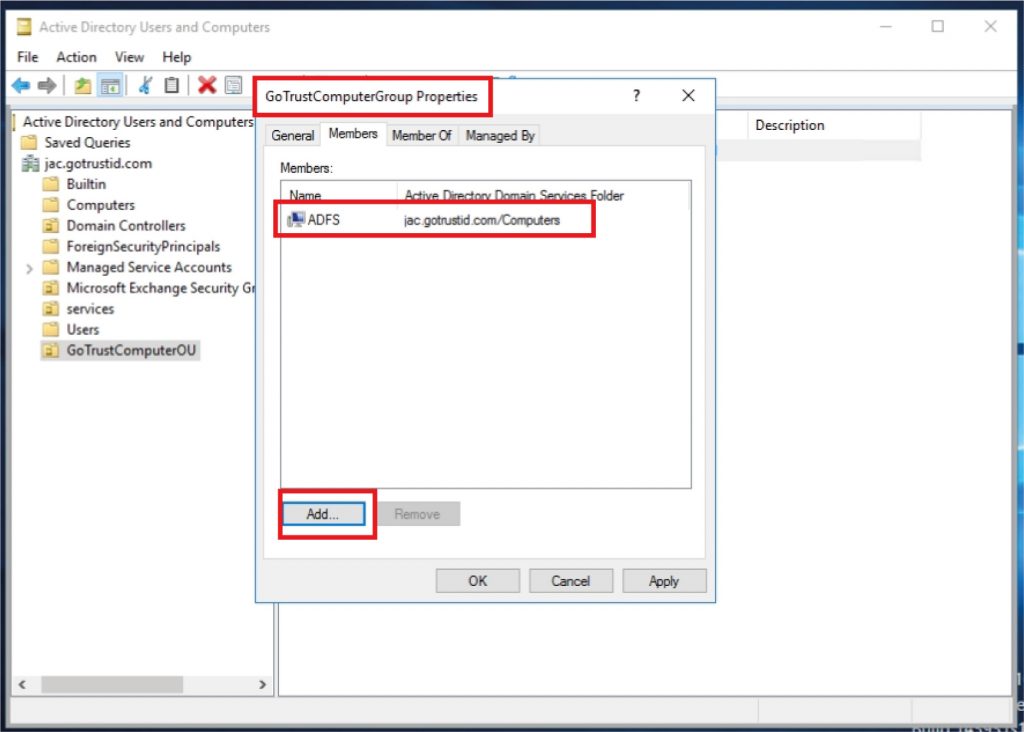
g. Navigate to the desired Organization Unit\SoftwareInstall, click “Add” and choose the desired Organization Unit to Security Filtering. Right-click “SoftwareInstall” and enable “Enforced”.
h. Navigate to the Organization Unit, and add the target computers to the Organization Unit. The target client computers need a reboot to apply the new GPO settings and install GoTrust ID desktop application.
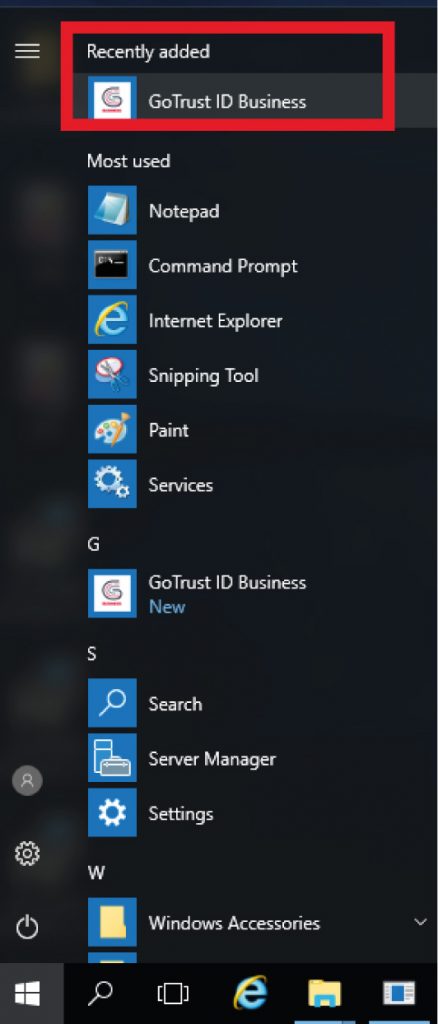
i. GoTrust ID desktop application will be shown in the recently added list after rebooting.
Learn more about installing software using Group Policy from Microsoft Support.
a. Navigate to “Computer Configurations\Policies\Software Settings\Software installation, right-click the target software, click “Remove” under “All Tasks”, and press “OK”.
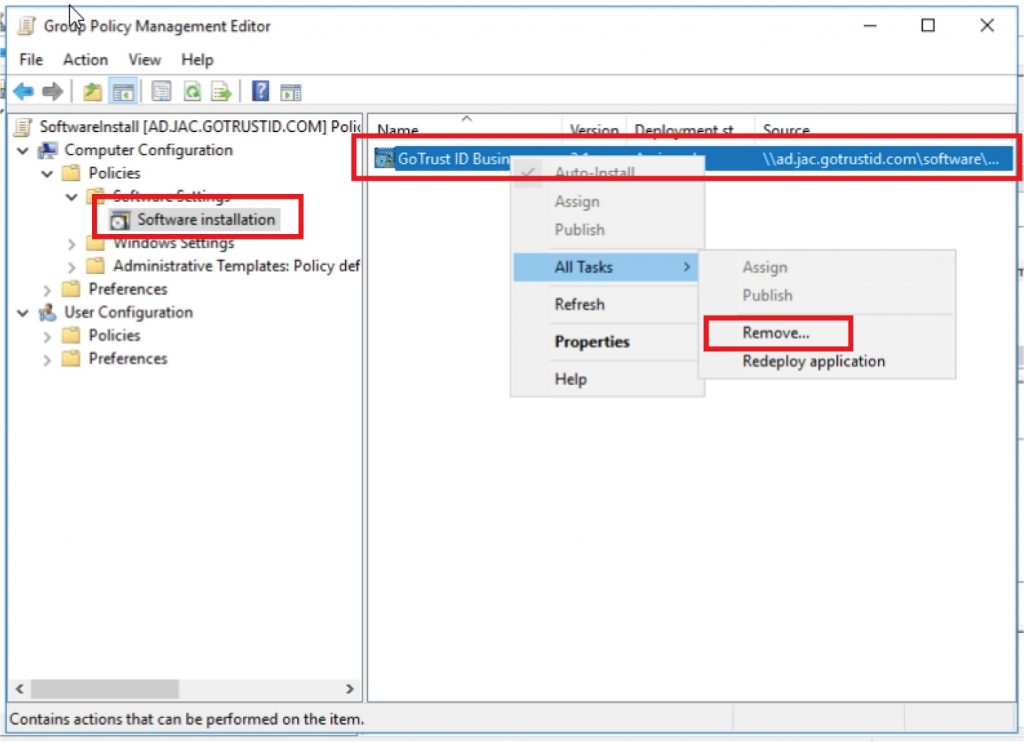
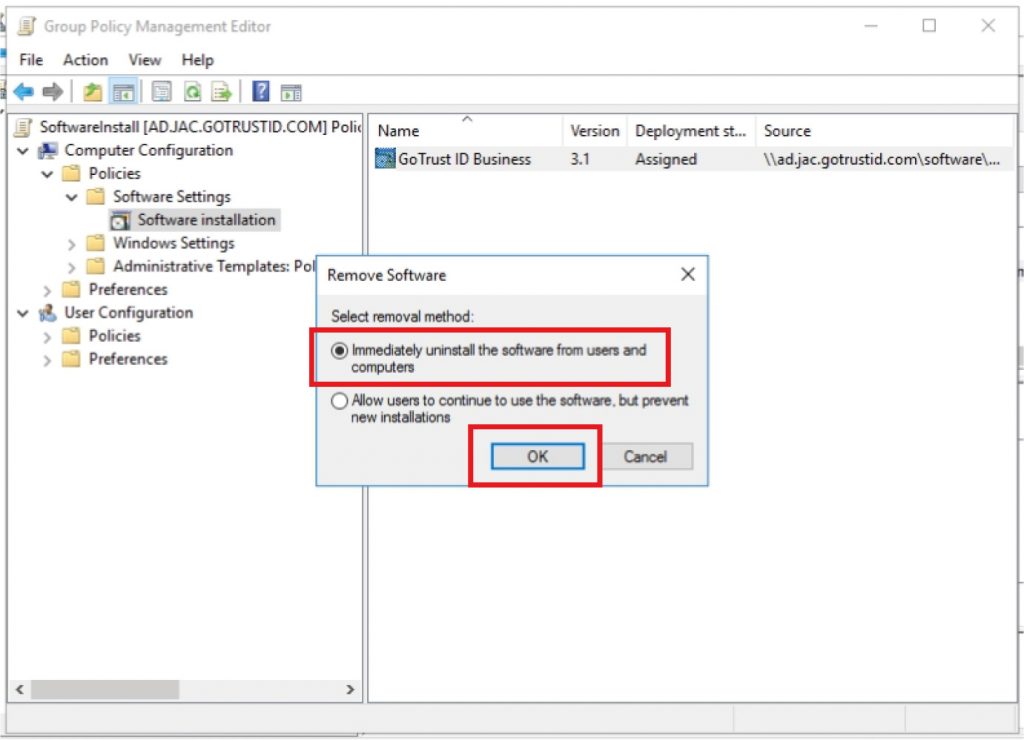
b. The target client computers need a reboot to apply the uninstallation.
Yes, company can use its software deployment utilities to deploy GoTrust ID desktop application.
3. Enrollment
Please make sure you have passed biometrics verification on the phone right after scanning QR code. PC screen will show “Register Successfully” once biometric authentication on the phone has been verified and phone has completed registration with authentication server.
If problem still exits, please check the connection environment between phone and authentication server.
Please insert your Windows device login password.
Normally one user license account can register 5 computers maximum.
You can enroll multiple phone authenticators to login your Windows device.
4. Server Configuration
GoTrust ID authentication server can run in an on-premises or cloud environment.
Yes, GoTrust ID authentication server supports High Availability (HA) structure to ensure a level of operational performance.
GoTrust ID authentication server can run on Windows server or Linux server.
Accurate and reliable time is highly important for server, PC and phone. Time discrepancy will result in login error. Please use Network Time Protocol (NTP) or other practical method to set correct time for authentication server.
Idem Key can be used for Azure AD managed Windows 10 devices. If your computer is not managed by a corporate Azure AD, you cannot use Idem Key to login Windows. To get more information, please refer to https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key-windows#enable-with-a-provisioning-package.
Yes. To use Idem Key on Linux, an additional configuration is required. You can refer to the document “How to use PAM with Idem Key on Linux”.
Yes. Idem Key is very secure. Idem Key embeds a secure element which is certified by Common Criteria EAL5+ and FIPS 140-2 Level 3. All cryptographic are handled inside the secure element and keys are stored in the secure element. Besides, Idem Key itself also certified by FIDO2 security level 2.
Please ensure that you put Idem Key at right place of NFC antenna on your Android phone. You can download the NFC app from Google Play such as “NFC TagInfo” to scan Idem Key and check the right location of NFC antenna.
Yes. Idem Key supports USB Type-C enabled computer. All you need is to use a USB-A (Female connector) to USB-C Type (Male connector) adapter with Idem Key.
Windows 10 version 1903 and later versions support the management of FIDO2 security key. You can use management console in “Windows Settings” -> “Accounts” -> “Sign-in Options” -> “Security Key”. Please refer to the video:
We recommend using at least 2 Idem Keys to register your web account as backup. Besides, most web services provide alternative 2-factor sign in options such as recovery codes or one-time codes.
Yes, Idem Key is IP68 rated. Idem Key is made by insert molding process and it sustains damage from water and dust.
All FIDO security key enabled web services can use Idem Key such as Google, Microsoft, GitHub, Dropbox, Facebook, Box and many more.
To use Idem Key, you do not need to install any driver or software. Idem Key is a driver-less product which can work on Windows, macOS, Linux, Chromebook, and Android.
There is a PIV application installed in Idem Key Plus and Pro. You can use any PIV compliant middleware such as OpenSC, Windows built-in minidriver, or macOS CryptoTokenKit to access PKI functions over USB or NFC interfaces.
Yes. You can reset your Idem Key on Windows 10 and all data in Idem Key will be erased. As for the reset procedure, please refer to the YouTube video: https://www.youtube.com/watch?v=Skx8s5C95c0
Yes. You can manage Security Key PIN of Idem Key on Windows 10.
Step 1. Go to “Settings” → “Accounts” → “Sign-in options” and find button “Manage” of “Security Key”
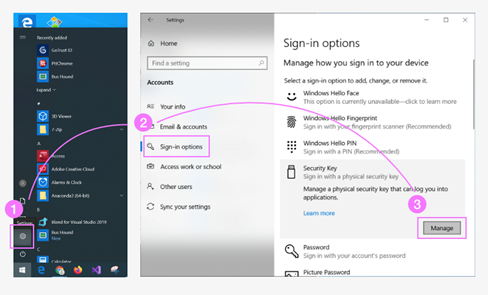
Step 2. Touch your Idem Key
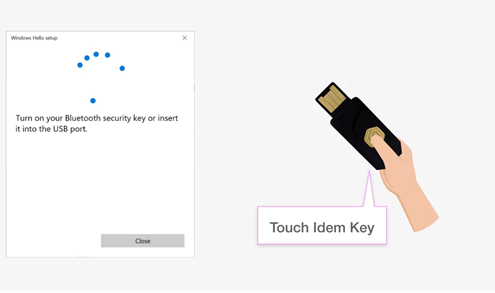
Step 3. Add New Security Key PIN
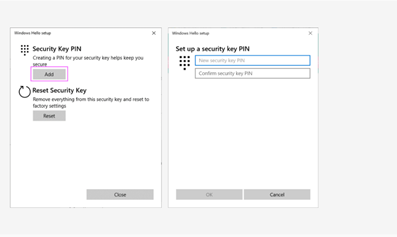
For security reason, Idem Key will prohibit reset command after powered on 10 seconds. We suggest that you re-insert Idem Key during the reset process. Please refer to the video: https://youtu.be/Skx8s5C95c0
You can download from the link below:
Attestation root certificate: https://www.go-trust.com/download/fido_metadata/idem_key/GoTrust_IdemKey_RootCA.pem
Metadata: https://www.go-trust.com/download/fido_metadata/idem_key/GoTrustID_IdemKey_12042019.json
Please refer to the video: https://www.youtube.com/watch?v=u5JLYN7H6-M
Yes. Idem Key supports the public key types “ecdsa-sk” , along with corresponding certificate types. By the way, OpenSSH version should be 8.4 or above. For more information, please refer to the application note “How to user SSH with Idem Key“
To utilize your Idem Key with Windows BitLocker for disk encryption, it is essential to first install the Idem Key Minidriver. This ensures seamless integration with Windows security features, including BitLocker. After the installation, you’ll need to generate a BitLocker certificate. This certificate can then be easily written to your Idem Key using the Idem Key Manager software. Together, these steps enable the use of your Idem Key for securely unlocking encrypted drives, combining the robust security of smart card technology with BitLocker’s encryption capabilities.
If you charge an Idem card one time per month, the battery will still have 80% of the original capacity after ten years. In other words, the operation time will be decreased by ~20%, but the battery will be still alive. However, if you charge an Idem card every day, the battery life cycle would be around two years. Therefore, please do not charge your Idem card frequently. If possible, please charge your Idem Card until the low battery indicator LED is flashing.
No. We do not recommend using conventional card printer since there is battery in Idem Card and conventional card printer will cause high temperature which is harmful to battery. If you need to print, you can use UV printing which prints under normal temperature. GoTrust also provide service to print customized artwork on Idem Card for mass deployment. You can contact support@gotrustid.com for more detail.
If you use latest Windows 10 version 1903 or above, there’s no additional driver required. Latest Windows 10 already support FIDO2 over BLE and NFC natively.
No. Because Chrome and macOS do not support FIDO BLE protocol, Idem Card cannot be used on macOS.
Windows 10 version 1903 and later versions support the management of FIDO2 security key. You can use management console in “Windows Settings” -> “Accounts” -> “Sign-in Options” -> “Security Key”.
There is a PIV application installed in Idem Card. You can use any PIV compliant middleware such as OpenSC, Windows built-in minidriver, or macOS CryptoTokenKit to access PKI functions over ISO7816 or NFC interfaces.
Idem Card will be in standby mode and will keep consume small power when you’re not using it. After Idem Card is charged to full, the battery can sustain 120 days.
Yes. Idem Card is very secure. Idem Card embeds a secure element which is certified by Common Criteria EAL5+ and FIPS 140-2 Level 3. All cryptographic are handled inside the secure element and keys are stored in the secure element. Besides, Idem Card itself also certified by FIDO2 security level 1.
Idem Card supports MIFARE Plus by default. GoTrust have other versions of Idem Card to support different physical access systems such as HID and FeliCa. You can contact GoTrust support (support@gotrustid.com) to get more detail.
Yes, NFC can work properly if the battery is not charged.
Yes. Idem Card supports FIDO2 resident key and it can store 30 resident keys.









